

2026/02/07 16:58:21
移远RG501Q-EU 固件版本RG501QEUAAR12A06M4G_SAGM有无法收发短信的问题,更新到 RG501QEUAAR13A01M4G_04.200.04.200.zip即可。在openwrt里可以直接更新,操作方式
qfirehose -f 模组固件解压后的目录/ -p 注意期间不能断电不能终止 ,否则可能会变砖,最后显示 Upgrade module successfully. 就表示升级成功了
2026/02/03 09:15:52
搞信创,应用开发两年测两年,刚上线,操作系统就进入扩展支持期了。。。
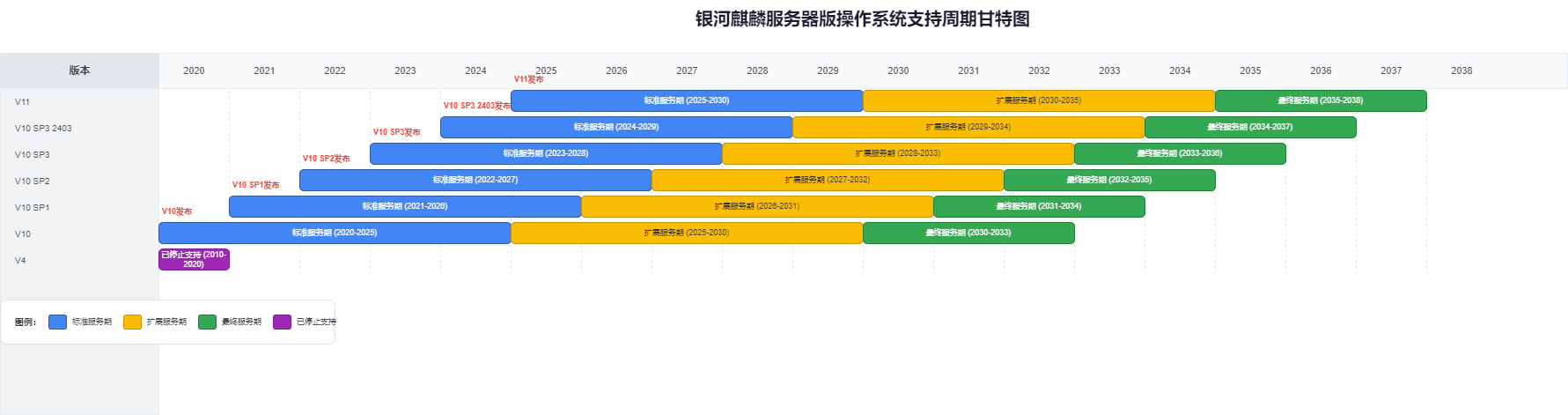
2026/01/30 16:37:57
GaussDB新推出了个k8s云化的版本 ,叫 CCE敏捷版(CCE Agile) ,本质上是用k8s管理很多容器,把这些容器当成主机放到tpops里纳管,但优势就是这些容器有一整套k8s的管理工具。不过看了下官方文档,安装起来似乎贼麻烦
2026/01/19 09:31:07
配置vscode的java调试环境语言为英文,避免中文乱码:
打开设置,搜索`java.debug.settings.vmArgs`,配置值为`-Duser.language=en -Duser.country=US`
2026/01/16 14:12:05
一个神奇的ORACLE BUG
select d.dummy
from (select case when exists (select 1 from dual) then '1' end c1 from dual) v
left join dual d
on (d.dummy = v.c1 or d.dummy = '2');执行后,连接直接断开
2026/01/10 19:50:53
停电几个小时,UPS的电都没了,本网站服务器不间断工作一年多,终于也重启了一回
2026/01/09 15:23:46
oracle如果对分区表append insert,没提交,再次insert会报错
ORA-12838: cannot read/modify an object after modifying it in parallel
2025/12/31 14:28:17
不知道有没有人写过,这里先记一下
oracle 可以使用savepoint,rollback能进行部分回滚,但是注意savepoint前后的事务id本身没有变化。观察v$transaction可以发现在savepoint后发生数据变更时,UBAREC的值会发生变化,UBA是undo block address的缩写,也就是说savepoint后改数据,会使用新的undo块地址,这样回滚时就能明确回滚到哪里截止
2025/12/26 14:01:02
openGauss手动执行单个regress的sql文件并对比输出是否一致
gs_guc reload -c "log_statement='all'"
cd $CODE_BASE/src/test/regress
gsql -q -a <sql/sw_prepare.sql >results/sw_prepare.out 2>&1
diff expected/sw_prepare.out results/sw_prepare.out
gsql -q -a <sql/sw_basic.sql >results/sw_basic.out 2>&1
diff expected/sw_basic.out results/sw_basic.out
gsql -q -a <sql/sw_clearup.sql >results/sw_clearup.out 2>&1
diff expected/sw_clearup.out results/sw_clearup.out
#注意初始化的字符序
gs_initdb --nodename=primary --pwpasswd=Gauss@123 --encoding=UTF-8 --locale=C2025/11/26 20:20:28
